Extortion Emails: How to spot & What to do
[4 mins read]
What are Extortion Emails?
Imagine this: You wake up one morning, tired and half-asleep, and you open your inbox to see a message that makes your blood run cold. The email claims that your private data has been stolen. Not just any data, but your most intimate secrets, the kind that could ruin your relationships, destroy your career, and humiliate you in front of everyone you know. The criminals demand a hefty ransom, threatening to broadcast your darkest moments to the entire world unless you comply. This isn’t some far-fetched plot from a thriller movie—it’s the reality of extortion emails.
These emails are a terrifying tactic used by ruthless cybercriminals to prey on your deepest fears. They exploit your worst nightmares, manipulating you into handing over money or sensitive information, all while you feel like you’re on the brink of losing everything.
What Do Attackers Aim to Achieve?
In short, extortion emails are carefully crafted to exploit your deepest fears and manipulate you into complying with the attackers’ demands, typically by requesting a ransom.
These emails are designed to prey on your personal vulnerabilities. Attackers often seek to inject paralyzing fear by convincing you they have compromising information, creating anxiety and urgency to respond or comply with their demands. Their primary goal is usually financial, with demands for ransom—often in cryptocurrency—to protect their anonymity and avoid law enforcement.
In many cases, they threaten to expose private photos, videos, or confidential data, leveraging the fear of reputational damage or harm to personal relationships. Additionally, by prompting you to click on malicious links or meet their demands, attackers can further compromise your systems or online accounts, gaining access to more data or installing malware, which increases their control and escalates the threat even further.
How to Identify Extortion Emails
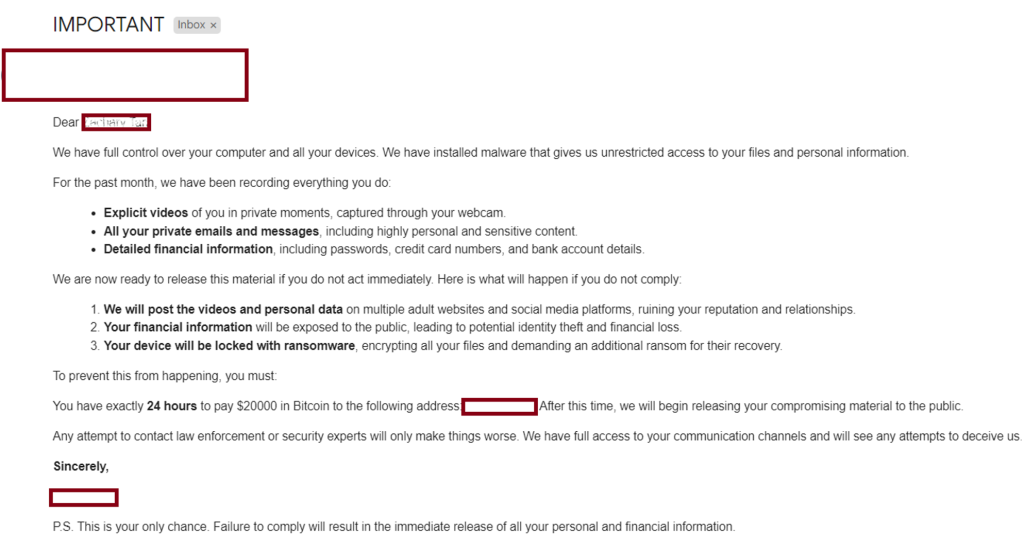
Example of an extortion email
Recognizing the signs of extortion emails is critical to avoiding panic and protecting yourself. Here’s what to look out for:
- Threats: The email will claim to have embarrassing information about you, such as photos or videos, that could ruin your reputation.
- Time Pressure: The attacker will often give a short deadline, like 24 or 48 hours, to create a sense of urgency and prevent you from thinking clearly.
- Payment Demands: The message will demand payment, usually in Bitcoin, with specific instructions on how to make the transaction.
- Technical Jargon or Claims: To sound more credible, attackers may claim to have hacked your webcam or gained access to your email account. They might even use your password in the email to scare you into thinking they truly have access to your systems.
- Email Spoofing: Email spoofing is a cyberattack technique where the attacker forges the sender’s email address to make the message appear as though it’s from a trusted source, to convince you that the attacker has taken over your account.
What to Do If You Receive an Extortion Email

Receiving an email like this can be terrifying, but you need to act calmly and decisively:
1. Do Not Engage or Pay the Ransom
Responding to these emails or paying the ransom only confirms that the attackers have your attention, making you a more attractive target. Paying doesn’t guarantee they won’t come back for more; it signals to the attackers that you are willing to comply, potentially leading to further harassment or even more extortion attempts. By paying, you also fund their operations, allowing them to refine their tactics and target you or others again in the future.
2. Change Your Passwords
If an extortion email contains a password you recognize, it likely means your credentials have been compromised. Even if no passwords are mentioned, it is still strongly recommended to change your password and delete the email. For added security, users should choose a strong password and enable two-factor authentication (2FA) whenever possible.
3. Make a Police Report
Reporting suspicious emails is crucial for combating cybercrime, especially if any payments were made. Reporting the crime helps document the incident in case the attackers continue their harassment. This may also help contribute by spreading awareness of ongoing cyber threats, potentially helping others avoid falling victim to similar cyber threats.
Singapore users may make a police report at their nearest Police Post, or Singapore Police Force (SPF) e-Services online.
4. Run Security Scans
It is highly recommended to run security scans using trusted antivirus software to detect and remove malware or other threats regularly. These scans can identify harmful programs or suspicious activity on your device, helping to keep your system secure and preventing potential breaches.
Prevention is The Best Cure
Preventing extortion emails is essential for safeguarding your digital life. The first step is to make sure that you are using strong, unique passwords of at least 12 characters, mixing letters, numbers, and symbols, while avoiding personal details or predictable patterns. You may consider using the free password checker to ensure that your password is strong enough.
Additionally, a password manager can help you securely generate and store these unique passwords, and enabling multi-factor authentication (MFA) adds an extra layer of security. Regularly update your software, operating systems, and applications to fix vulnerabilities that cybercriminals might exploit. Be cautious with unexpected emails, especially those that create urgency or threats—always verify the sender’s details and avoid clicking on suspicious links or attachments.
While the fear and anxiety caused by extortion emails can be overwhelming, it’s important to remember that you are not powerless. By understanding these threats and taking proactive measures, you can protect your privacy and avoid becoming a victim.
For more information on similar cyber threats and scams, click here or visit https://www.scamshield.gov.sg/. Take action, stay vigilant, and safeguard your digital life.
IT Tips | Email Security | Cybersecurity | Cyber Threats | Phishing | Scams | Password | Data Security | Data Protection
