Key Lessons from 7 Recent Ransomware Attacks
[4 mins read]
In recent years, businesses have increasingly relied on technology for their business processes. Ransomware attacks have also risen significantly, becoming the top concern for businesses worldwide.
In this article, we’ll take a look at seven recent ransomware incidents that have directly affected various industries in Singapore. Join us as we carefully examine each case and discover the important lessons we can learn from these real-world situations.
Recent Local Ransomware Incidents
Jumbo Group:
On 23 May 2024, The Straits Times reported that Jumbo Group, a well-known seafood restaurant chain based in Singapore, reported a recent ransomware incident. The relevant authorities, including law enforcement agencies such as the Singapore Police Force (SPF), the Personal Data Protection Commission (PDPC), and the Cyber Security Agency of Singapore (CSA), were immediately notified of the incident. The initial investigations indicated no evidence of data theft, and the company promptly activated its business continuity plan in response.
Mustafa Group:
The Mustafa group of companies, known for its operations including a shopping mall in Little India, faced a data leak incident. On 25 April 2024, a cyber attacker claimed on the hacker forum that they had stolen 180GB of personal information from Mustafa customers and employees, including full names, NRIC numbers, and home addresses. This incident has been reported to the relevant authorities and is currently under investigation by the Personal Data Protection Commission (PDPC).
Mustafa Group has also engaged external cybersecurity professionals to conduct a comprehensive review of its IT systems for improvement.
Shook Lin & Bok:
Reported in April 2024, Singapore law firm Shook Lin & Bok experienced a ransomware attack that was discovered on April 9, 2024. The firm immediately engaged a cybersecurity team and specialists to minimize the impact on clients and stakeholders. The incident was reported on 10 April 2024, to the Singapore Police Force (SPF), the Cyber Security Agency of Singapore (CSA), and the Personal Data Protection Commission (PDPC).
It was mentioned in another report, that the law firm allegedly paid US$1.4 million (S$1.89 million) in bitcoin to Akira ransomware group.
Aztech Global:
In February 2024, Aztech Global, a technology solutions provider, faced a cybersecurity incident involving unauthorized access to its IT network and a ransomware attack. The company promptly shut down servers during the Chinese New Year break and conducted cybersecurity screenings to prevent further data compromise. Reports were then lodged with the Singapore Police Force (SPF), the Personal Data Protection Commission (PDPC), and the Singapore Cyber Emergency Response Team (SingCERT).
Aztech Global has also hired forensic advisers to investigate the incident and is consulting industry experts to strengthen its cybersecurity measures. Aztech Global also released updates on 13 February, informing stakeholders that they have not faced any material impact financially or on its operations.
RE&S Holdings:
On January 11, 2024, RE&S Holdings, a Japanese multi-brand food and beverage operator listed in Singapore, reported a ransomware attack that compromised its servers. This incident has been reported to the Personal Data Protection Commission (PDPC).
Following the attack, the company promptly initiated data recovery processes and activated its business continuity plan, ensuring no significant impact on its business operations. Preliminary investigations, conducted with external experts, revealed no evidence of data exfiltration or compromise of sensitive personal information.
ES Group:
As reported on 2 January 2024, ES Group (Holdings) experienced a ransomware attack, announcing that the incident had affected most of its server data. However, they stated that the threat was contained, based on ongoing investigations. The attack did not significantly impact the company’s business operations, which continued as usual. ES Group activated its business continuity plan, disconnected its systems from the network, and enlisted external assistance for investigation, containment, and data recovery.
The incident was reported to the police, the Personal Data Protection Commission (PDPC), and the Singapore Cyber Emergency Response Team (SingCERT).
IPS Securex:
On 2 January 2024, IPS Securex Holdings reported a ransomware attack that rendered its network inaccessible. As a provider of security systems and services, the company began recovery operations and found no evidence of data being stolen during the attack.
In a 5 January 2024 update to the Singapore Exchange, IPS Securex revealed that the incident took place on 26 December 2023.
Important Lessons Businesses Should Learn From
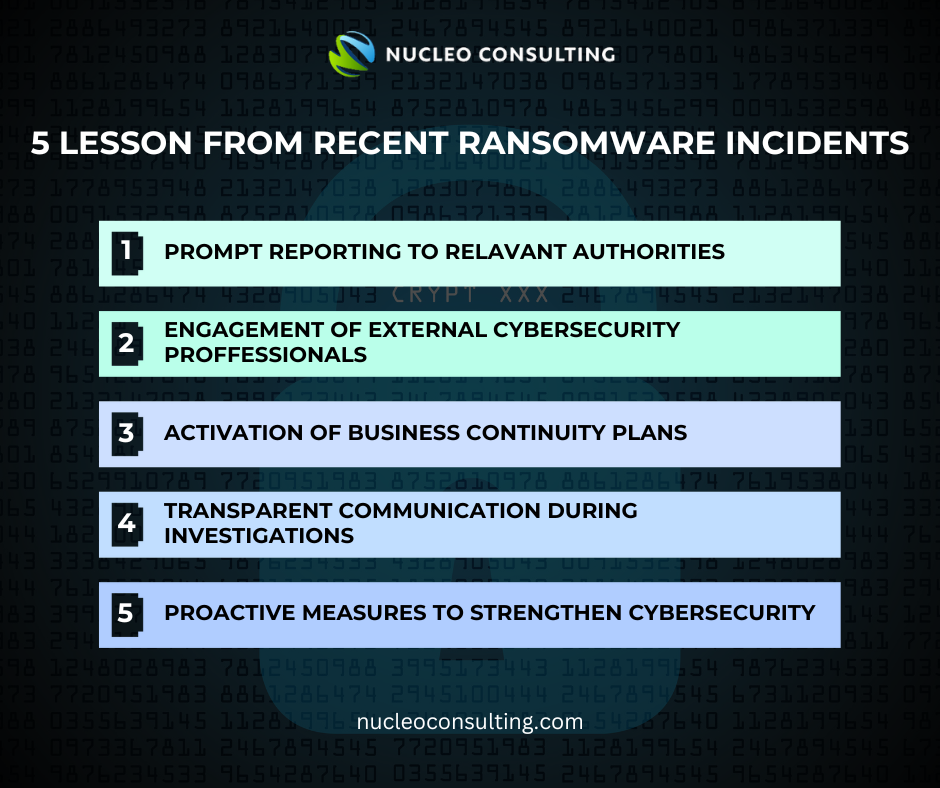
Prompt Reporting to Relevant Authorities
During a ransomware attack, promptly informing relevant authorities, including law enforcement agencies and regulatory bodies, is essential. Involving these authorities promptly not only enhances the likelihood of a successful resolution but also contributes to broader efforts in combating cyber threats and safeguarding businesses in the digital space. This swift action facilitates coordinated responses and investigations, crucial for mitigating the impact of cyberattacks.
Here are the list of important contacts to note of:
(a) Singapore Police Force (SPF)
(b) Cyber Security Agency of Singapore (CSA)
Engagement of External Cybersecurity Professionals
In an event of a ransomware attack, businesses should seek the expertise of external cybersecurity professionals. These experts can find out the extent of the attacks, contain the threats, and check all IT systems. This collaboration with professionals increases the chances of a successful resolution to the ransomware attack while minimizing downtime for the business. Cybersecurity Professionals should also be able to spot security vulnerabilities in IT systems and implement effective countermeasures to fortify defenses against future breaches.
Outsourcing cybersecurity services empowers businesses to stay ahead in the ever-evolving landscape of digital security, allowing them to focus on their core operations with peace of mind.
Activation of Business Continuity Plans
Businesses should not wait for an attack to happen to take action! To mitigate and minimize the damages of a ransomware attack, companies should have a comprehensive Business Continuity Plan. These plans involve several components, such as a dedicated Ransomware Incident Response Plan, temporary system shutdowns, network disconnections, and disaster recovery processes. These actions are taken to swiftly contain threats and reduce downtime. Ensuring reliable data backups is crucial for facilitating a swift recovery process.
Transparent Communication During Investigations
While preventing the ransomware from doing further damage is essential, businesses should also maintain transparent communication with stakeholders, providing updates on the progress of investigations and any significant developments related to the incidents. This transparency fosters trust and confidence among customers, shareholders, and regulatory authorities during times of crisis.
Proactive Measures to Strengthen Cybersecurity
In view of all the rising ransomware attack cases worldwide, businesses should continue to improve and fortify the security of their IT infrastructure. This includes steps like conducting Vulnerability Assessments (Pentesting, or Penetration Testing), forensic investigations, and consultations with industry experts, to enhance their resilience against future cyber threats. This proactive approach not only protects sensitive information but also demonstrates a commitment to cyber security, fostering greater confidence and loyalty among clients and stakeholders.
Conclusion
The recent ransomware incidents in Singapore have shown how important it is for companies to act quickly and use strong cybersecurity measures to prevent ransomware. Each case teaches valuable lessons on how businesses can improve their security and prevent cyber attacks before they strike.
Prevention is better than cure. Businesses with strong cybersecurity protocols are more likely to build stronger relationships with clients, investors, and stakeholders. Don’t let the cyber threats ruin the reputation you have spent years building.
IT Tips | News | Ransomware | Data Leak | Cyber Security | Cyber Threats | Business Continuity | Pentesting | VAPT
