NuMonitor offers advanced remote monitoring and patch management features designed to safeguard your business with real-time ransomware detection. It equips your business with the robust security it deserves, ensuring peace of mind and uninterrupted operations in the face of evolving cyber threats.
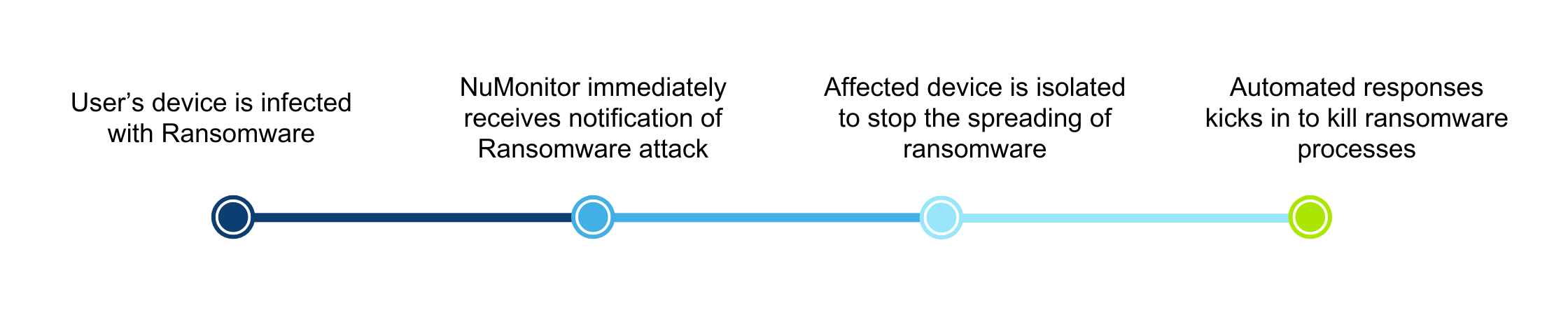
Ransomware Isolation Demonstration

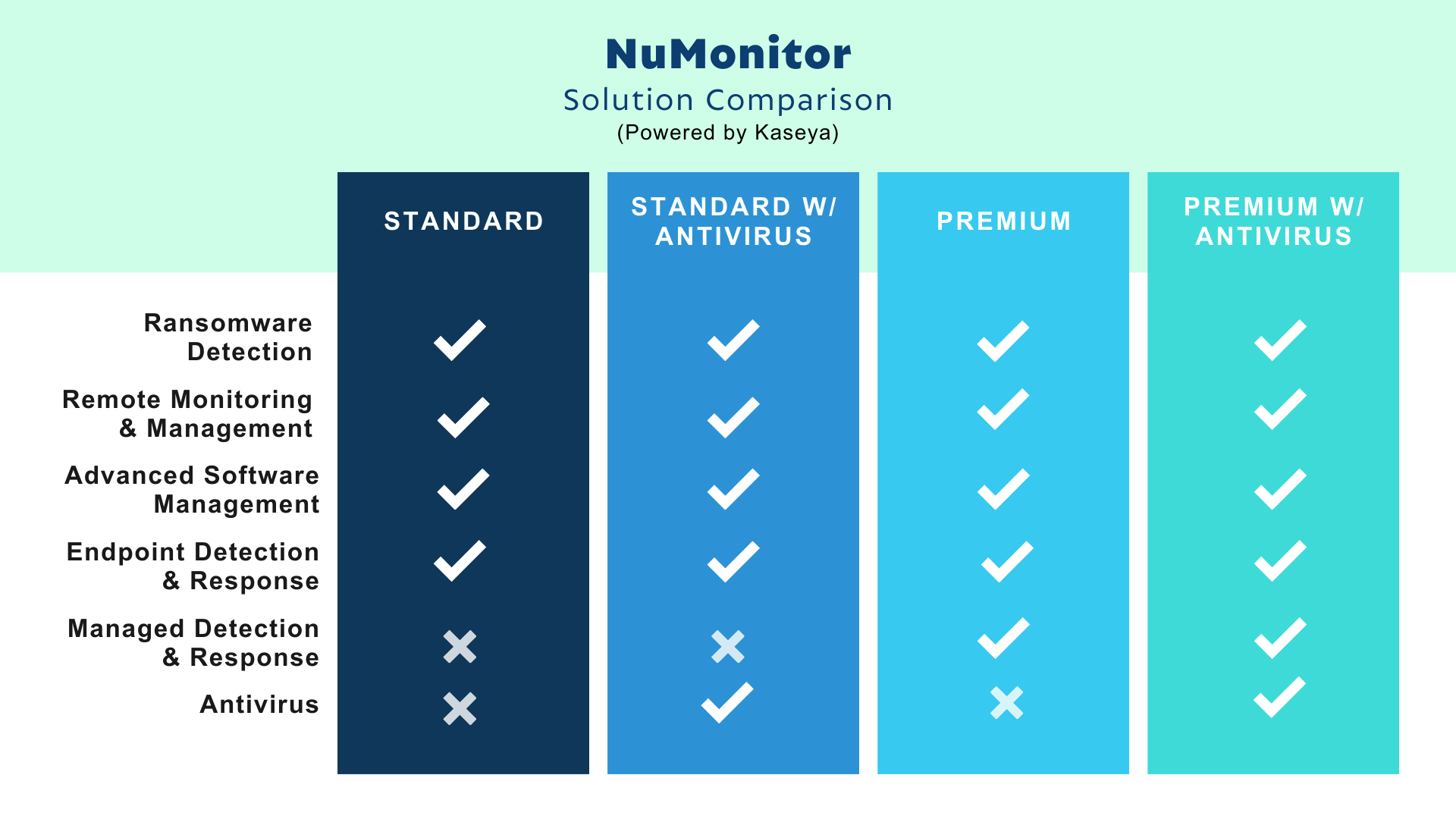
Ransomware Detection

Remote Monitoring & Management

Advanced Software Management
Endpoint Detection & Response (EDR)

Managed Detection & Response

AntiVirus
Ransomware Response
Case Study
Scenario 1:
An Employee, Alice, is traveling for a business trip and connects to the public Wi-Fi at a hotel. Unaware that the Wi-Fi network has been compromised and is being used to distribute ransomware.
Scenario 2:
A large organization with 10 branches employs thousands of users. An employee at one of the branches, Bob, receives a phishing email and inadvertently downloads a ransomware.
Resolution:
Network isolation and remote access enable technicians to swiftly neutralize ransomware threats before the user returns to the company and spreads the ransomware across the company’s network. With ransomware detection in place, automatic responses kick in to kill the ransomware process.
Resolution:
With the network isolation coupled with remote access capabilities, technician are able to isolate the infected device while preventing the ransomware from spreading across the network to the other branches and Headquarters.
Scenario 1:
An Employee, Alice, is traveling for a business trip and connects to the public Wi-Fi at a hotel. Unaware that the Wi-Fi network has been compromised and is being used to distribute ransomware.
Resolution:
Network isolation and remote access enable technicians to swiftly neutralize ransomware threats before the user returns to the company and spreads the ransomware across the company’s network. With ransomware detection in place, automatic responses kick in to kill the ransomware process.
Scenario 2:
A large organization with 10 branches employs thousands of users. An employee at one of the branches, Bob, receives a phishing email and inadvertently downloads a ransomware.
Resolution:
With the network isolation coupled with remote access capabilities, technician are able to isolate the infected device while preventing the ransomware from spreading across the network to the other branches and Headquarters.