Uncovering the Top 10 Prevalent Ransomware
[5 mins read]
Technology is a double-edged sword, with cyber attacks growing more sophisticated as technology advances. Ransomware, in particular, remains a top concern for businesses worldwide.
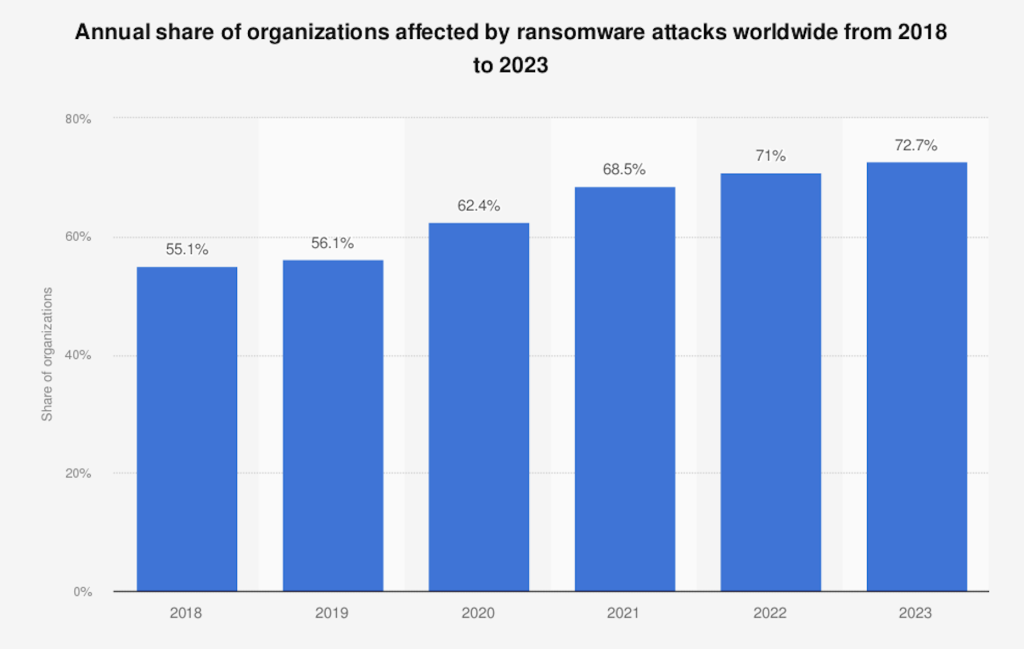
(Statista, 2023)
Statistics show a steady rise in cases of ransomware attacks worldwide. Over 72% of businesses have been affected by ransomware attacks in 2023. Ransomware attacks businesses by infiltrating their system through various methods. A ransomware attack results in paralyzed business operations and causes serious operational downtime, damage to reputation, and devastating financial losses.
Unfortunately, there is no guarantee that the files will be restored even after paying the ransom, and businesses may even face repeated attacks. The sophistication and frequency of these attacks make them a persistent menace, striking fear into the hearts of business owners and IT managers who must constantly be on guard to protect their digital assets. Hence, it’s important to know and recognize and understand the threats.
What is Ransomware?
Ransomware is a type of malware designed to infiltrate computer systems and encrypt files or lock users out of their devices, rendering them inaccessible. Once inside, the ransomware locks important files and demands a ransom to unlock them. Businesses either pay the ransom or spend a lot of time and money trying to fix the damage.
These attacks can have devastating consequences for individuals and businesses, leading to the loss of critical data, operational downtime, damage to reputation, and significant financial losses due to extortion payments or recovery efforts. Ransomware attacks often exploit vulnerabilities in software or rely on social engineering tactics, such as phishing emails or malicious links to gain access to systems.
Top 10 Most Prevalent Ransomware:
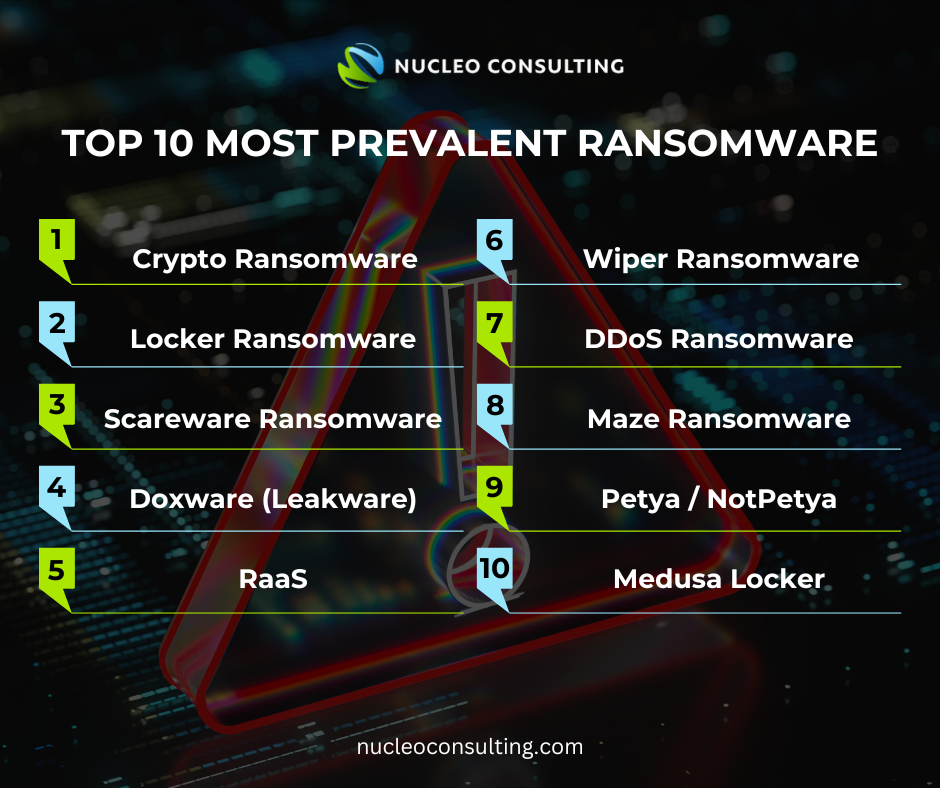
- Crypto Ransomware
Crypto ransomware is a type of malware that encrypts files on a victim’s computer or network, making them inaccessible. The attacker then demands a ransom, typically in cryptocurrency like Bitcoin, in exchange for the decryption key to unlock the file.
As the name suggests, this type of ransomware uses cryptographic techniques to encrypt the files, making them unreadable without the decryption key. Some well-known examples include WannaCry and CyptoLocker.
- Locker Ransomware
Unlike Crypto Ransomware, Locker Ransomware doesn’t encrypt files. Instead, it locks users out of their devices entirely. Imagine someone locking you out of your home, leaving you no access to your belongings. The person who locked you out then demands a ransom for accessing your belongings. Frustrating and scary, isn’t it?
This type of ransomware usually displays a message or screen that prevents users from accessing their device or data until the ransom is paid. Locker ransomware may lock the entire system preventing users from logging in, or it may lock specific files or folders.
- Scareware
This ransomware is a deceptive form of malware that preys on the victims’ fears by pretending to be legitimate security software. Once installed on a system, it employs social engineering tactics, bombarding users with pop-up alerts and fake virus detection messages, tricking them into believing that their device is infected.
The scareware ransomware would then demand payment to “resolve” the fabricated issues. However, scareware ransomware typically does not cause any real damage to the system, instead, it capitalizes on psychological manipulation to coerce victims into paying for unnecessary services or software.
- Doxware (Leakware)
Doxware, also known as Leakware, is malware that focuses on stealing sensitive data from the victim’s systems instead of encrypting them. This stolen information, which may include personal or confidential data, is then threatened to be released publicly unless a ransom is paid.
This can be highly damaging to both individuals and businesses, as it can lead to reputational damage, financial loss, and legal consequences.
- Ransomware-as-a-Service (RaaS)
Ransomware-as-a-Service (RaaS) is a cybercriminal business model where developers offer ransomware tools and infrastructure to affiliates. This allows individuals without technical skills to deploy ransomware attacks. Professional hackers handle the execution of the attack and share the profits with their clients. This model has contributed to the spread of ransomware attacks, making them more accessible to a wider range of cybercriminals.
- Wiper Ransomware
Wiper ransomware represents a particularly malicious form of cyber threat that diverges from conventional ransomware tactics. Unlike typical ransomware that aims to extort money from victims, the Wiper ransomware’s primary objective is to cause irreparable damage by permanently deleting or corrupting data. It operates with the intention of inflicting maximum harm, often as part of cyber warfare or vendettas. When launched, Wiper ransomware indiscriminately wipes out files and systems, rendering them unusable and causing chaos.
- DDoS Ransomware
This type of ransomware combines ransomware with Distributed Denial of Service (DDoS) attacks. It operates by overwhelming a network with traffic, effectively rendering it inaccessible to legitimate users, while simultaneously demanding a ransom to halt the attack.
This dual-threat tactic poses significant challenges for victims, as they not only face the encryption of their data, but also have to endure network downtime until the ransom is paid.
- Maze Ransomware
Maze ransomware stands out for its unique approach, combining 2 common ransomware tactics:
(i) Encrypts files
(ii) Locks users out of their devices.
It not only encrypts sensitive data, making it inaccessible to users, but also extracts that data from targeted systems. This unique approach significantly increases the stakes for victims, as Maze threatens to release their confidential information if ransom demands are not met. First appearing in 2019, Maze has since targeted various industries worldwide, including healthcare and finance.
- Petya/NotPetya
Petya Ransomware was initially spread through infected email attachments, with a primary focus on Windows systems. It encrypts critical components like the Master Boot Record (MBR) and the Master File Table (MFT), rendering all data on the drive inaccessible to victims. NotPetya ransomware is a more destructive variant of the Petya Ransomware, designed to cause widespread disruption and maximum damage, prioritizing damage over financial gains.
- MedusaLocker
MedusaLocker ransomware is a potent strain known for encrypting files on infected systems and demanding payment for decryption, noted for its ability to spread rapidly across networks. MedusaLocker disrupts business operations by rendering files inaccessible, posing significant challenges for victims seeking recovery.
In the face of ransomware threats, vigilance is vital. The road to ransomware recovery is both difficult and costly. Establishing proactive cybersecurity measures, safety protocols, and a comprehensive disaster recovery plan is crucial for safeguarding your business. Your awareness and proactive actions are key defenses against potential attacks, ensuring the protection of your organization’s data and business operations.
IT Tips | Ransomware | Ransomware Detection | NuMonitor | Cybersecurity | Cyber Threats
