Fun Facts of Technology
[2 mins read]
So you think you know everything about technology? Let’s see how many of these facts you know!
Some of them may even surprise your fellow colleagues in the IT department!
1. The first Apple logo
Nope, Apple’s logo did not start off with an apple! In fact, the apple was only a tiny part of the whole logo, which was designed by Ronald Wayne. His logo consists of an image of Isaac Newton sitting under a tree, with an apple that is about to fall onto his head.

Neither Ronald Wayne nor his logo lasts long at Apple. In the year 1977, merely a year later, Steve Jobs hired Rob Janoff to create a more modern-looking logo that would resemble and blend in with the name “Apple”.
2. Samsung is older than Apple
Samsung was founded on 1 March 1938, by Lee Byung-Chull in Taegu, Korea.
Apple was founded on 1 April 1976, by Steve Jobs and Steve Wozniak in Los Altos, Califonia, United States.
To be exact, Samsung is 38 years and 1 month older than Apple!
3. What comes after Terabytes
You may have come across terms like kilobyte (KB), megabyte (MB), gigabyte (GB), or even terabyte (TB). Most of us don’t own any data greater than a few TB, but in case you didn’t know, there is a proper name for such huge data.
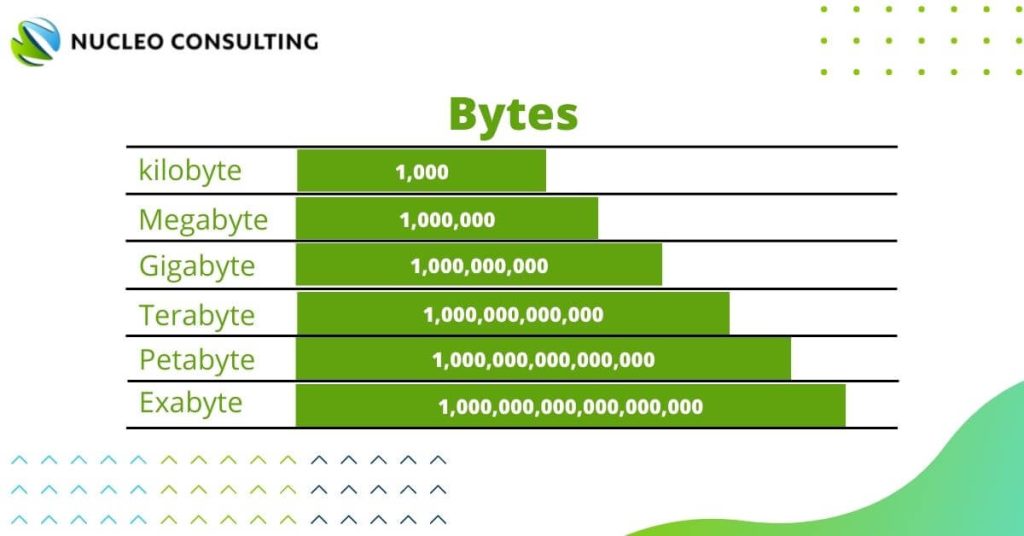
As you may know:
- 1 000 kilobytes (KB) = 1 Megabyte (MB)
- 1 000 Megabyte (MB) = 1 Gigabyte (GB)
- 1 000 Gigabyte (GB) = 1 Terabyte (TB)
And as you have guessed, there are 1,000 terabytes in a petabyte and 1,000 petabytes in an exabyte. That is a lot, a lot of data!
4. The first computer mouse

Invented in the year 1964 by Doug Engelbart, the very first computer mouse back then looked nothing like the ones you are using. It was made out of wood and was rectangular in shape, with a little button at the top. He named it a ‘mouse’ as the cords resemble tiny rodents.
5. Computer Security Day
Yes, there is National Computer Security Day!
It started in the year 1988, to raise public awareness of cyber threats, cybersecurity, and other issues relating to computer security.
This day is celebrated by ensuring that your computers and data are all properly secured, making sure that your devices and software are updated. And also serves as a reminder to focus and ensure that the cyber security of your devices is in place.
6. It’s a boy!

An android literally refers to a robot that resembles a man. And yes, there is a proper term for the female version- Gynoid.
7. More than 300,000 new malicious files per day
In the year 2020, Kaspersky released news that it has detected an average of 360,000 new malicious files on a daily basis, throughout the year!
As technology advances, this number is expected to increase significantly. Make sure you pay attention to the cybersecurity of your computer and all other devices!
8. The ‘Real’ Traffic
Most of us can’t do without the internet. However, cyber attacks can’t happen without the internet too.
Did you know, that only about 39% of internet traffic is from humans? Unfortunately, the other 61% is from hacking tools, bots, and other non-human sources.
If you still think cybersecurity is not necessary for you or your business, think again. The results of any cyber attack will be disastrous!
9. The first computer virus

The Creeper program– Developed in 1971 by Bob Thomas of BBN. It was identified as the first computer virus created. Creeper was originally created to test out the cybersecurity to see if a self-replicating program was possible. This program had no cyber criminal intentions but only displayed a simple message to those who were infected.
10. Tonnes of e-waste generated annually
Singapore generates more than 60,000 tonnes of electronic waste (e-waste) annually. This number is expected to increase significantly as technology advances. Singapore has also stepped up to gain awareness of various e-waste recycling programs.

E-Waste has become a common issue globally. Individuals are encouraged to reduce e-waste by making sure that the faulty device is beyond repair before throwing it out. Those devices that are still in working conditions can be reused or donated. Also, consider recycling e-waste before throwing it right into the trash!
